| Please note: For privacy reasons the identity of the hacked account in the example used for this blog has been changed.
In our previous email security education blog we reviewed trending email security threats. In this blog, we’d like to show you what a phishing campaign looks like, and its scary consequences.
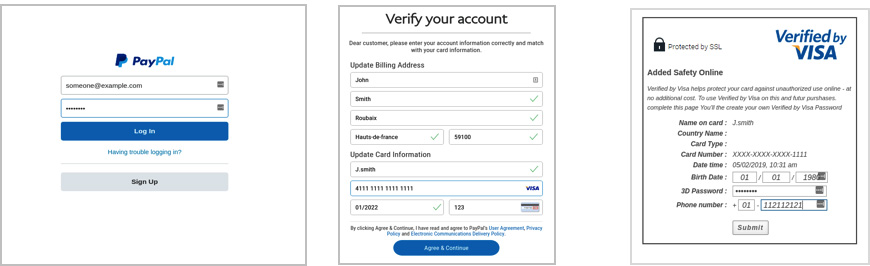
In this example, the hackers are pretending to be PayPal, informing users their account access has been locked and the account suspended due to security reasons. To restore account access, they request users to click on the link in the email to confirm their personal details. So how do you spot this is a phishing email?In the “From†field notice that the sender is not a standard PayPal address, but: “servicems@xxxâ€. Clicking on the link takes you to the following site:
While this may look like a PayPal page, notice the URL: “mk/ShadowZ118/public/myaccount/signin/?country.x=FR&locate.x=en_FRâ€. If this had been PayPal, you would have seen a legitimate PayPal URL. Looking at the email headers (view email headers) in the image on the right will also show telltale signs that this is not a legitimate PayPal website. For example, below:
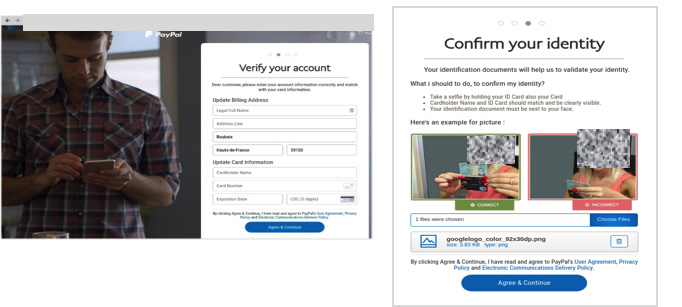
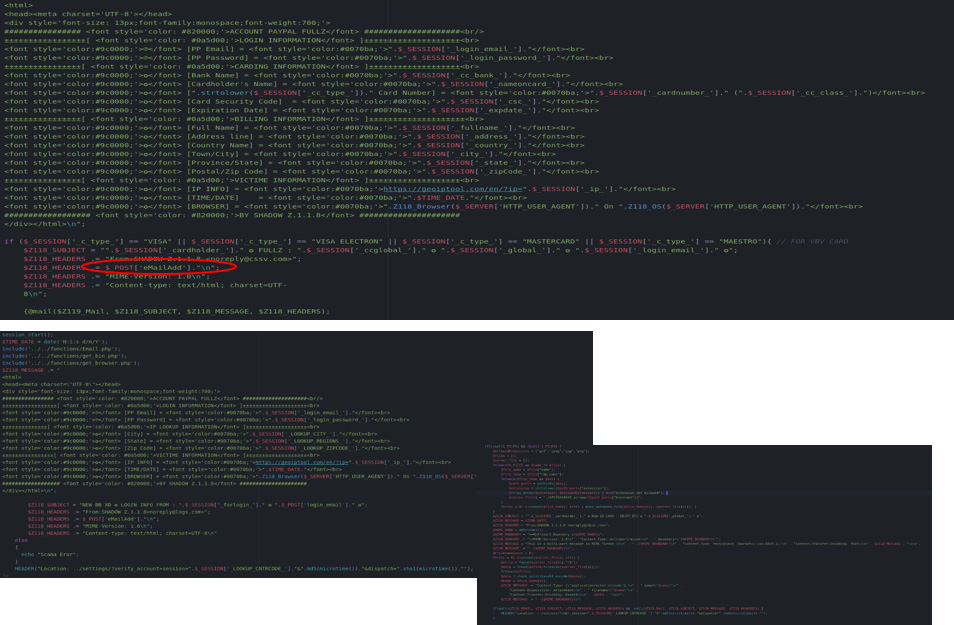
Here is an example of what the “senddd.php†looks like. As you can see this is a standard PHP custom mailing script that comes in all shapes and sizes, where the bad actors are able to set the subject, from, and content fields to anything they desire. In the “Maillist†field the hacker will add an entire list of email addresses found using one of the methods mentioned above (e.g. scraping). Normally the email server does not belong to them, and hence they don’t care if it gets blacklisted. When users log in to the fake “PayPal site†and continue to complete all their account and personal information (see below screenshots) the bad actors get access to all their information, which is auto saved on the site the bad actors use. This is an example of an advanced phishing kit, where not only basic information is requested but also passwords, credit card information, and screenshots of passports.
As users complete their credit card information the bad actors save all the information in the back end with the help of a little PHP script. Looking closely at the script in the image below, we can see the scammers are saving all the vital information they need to commit fraud then simply sending all the information to their own email address.
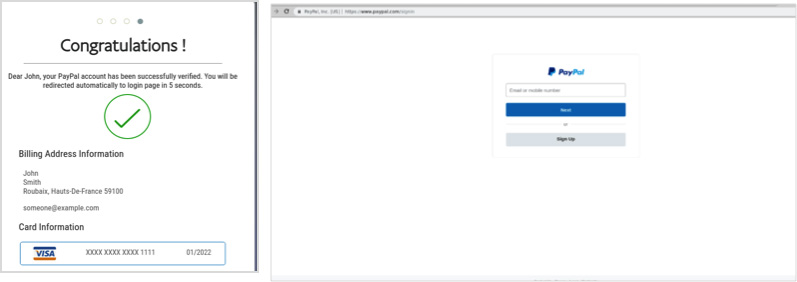
Finally, users receive a confirmation that their account has been successfully “verified,†and are automatically redirected to the PayPal official site. Meanwhile, the bad actors have saved their personal information, including credit card numbers, passport photos, and relevant passwords—all that is needed for the bad actors to inflict damage.
As seen in this blog, acting on phishing emails could have severe consequences. With that in mind, here are four steps you can take to help protect yourself:
If you are looking to protect email against phishing attacks, including other email-borne threats, start a trial with Freelance Computers using Mail Assure today and see how we can help keep your inboxes clean.
|
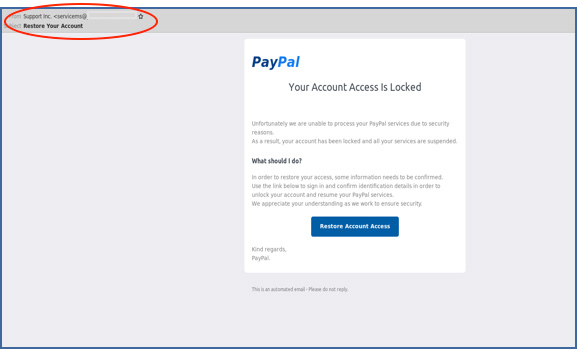 Bad actors (hackers, spammers, scammers, etc.)Â
Bad actors (hackers, spammers, scammers, etc.)Â 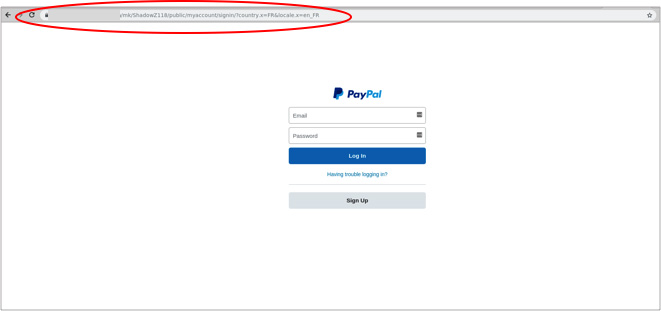
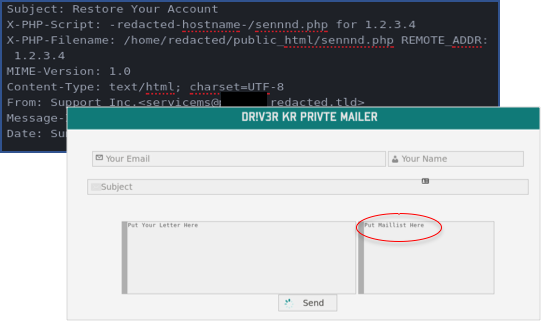 X-PHP script of “senddd.php†is not something that PayPal would ever use
X-PHP script of “senddd.php†is not something that PayPal would ever use